Trezor Login – Secure Access with Hardware Wallet Authentication
This page explains how the Trezor login process works and how authentication is handled through secure hardware design. It outlines what “login” means in the context of a Trezor wallet, covering PIN protection, passphrases, device confirmation, and recovery principles. All information here is educational, non-interactive, and designed for clarity and SEO compatibility.
Understanding Trezor Login
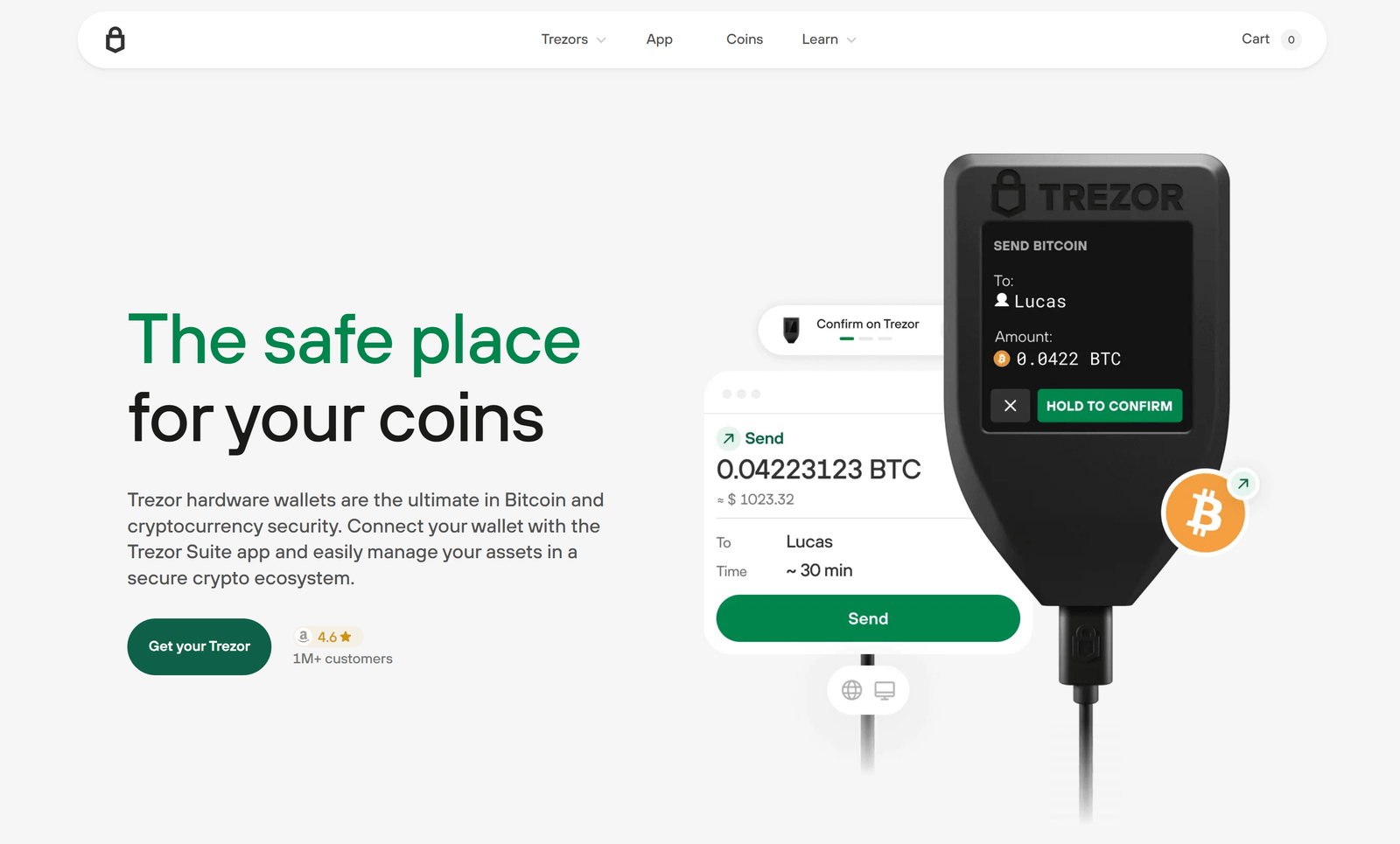
The concept of “logging in” with Trezor differs from traditional password-based websites. A Trezor device is a hardware wallet, not an online account. It holds private keys securely within its chip and never exposes them to the computer or internet. Access is verified through a local unlock using the device itself. Once the wallet is unlocked, a compatible application can display balances or initiate transactions — but only after you approve them on the physical device.
Local Authentication Through PIN
The first layer of protection is a PIN code. This numeric code ensures that only authorized users can unlock the device. Entering the wrong PIN repeatedly increases delay times, discouraging brute-force attempts. The PIN never leaves the device, and it is not transmitted or stored elsewhere. It is strictly a local safeguard that protects physical access to your wallet.
Each time the Trezor is connected, you are prompted to unlock it using the PIN. This step grants temporary access to manage assets but does not create an online session. Even when the device is connected, no sensitive information leaves its secure chip.
Passphrase: Optional Layer of Security
An advanced user may enable a passphrase — sometimes referred to as the “25th word.” This feature creates an entirely new wallet derived from the same recovery seed but protected by a custom phrase. The passphrase adds privacy and flexibility, allowing multiple wallets on the same device. It is never stored or transmitted, and losing it means permanent loss of access to that wallet, so it must be handled with care.
Device Confirmation: Human Verification for Every Action
Whenever you perform a critical action such as sending funds, the device itself requests your confirmation. The display on the Trezor shows the transaction details — addresses, amounts, and fees — for you to review. You must physically approve the transaction before it is signed. This step ensures that even if the connected computer is compromised, the attacker cannot move funds without your explicit, physical confirmation on the device.
Hardware Security and Local Processing
All cryptographic operations take place inside the hardware wallet. The private keys never appear outside the secure chip. The companion software (such as desktop or web interfaces) only facilitates interaction and displays data from the blockchain. This separation is the core of hardware wallet security — the computer never has the ability to sign transactions directly.
Because of this design, “login” should be understood as device authentication rather than server authentication. You log into the hardware wallet locally, not into a remote website or service.
Recovery and Backup
During setup, your device generates a recovery seed — typically 12, 18, or 24 words. This seed is the only way to restore access if the hardware wallet is lost or damaged. It must be written down and stored offline in a safe location. The recovery phrase should never be entered on a computer or phone. All official recovery actions occur directly on the device display, ensuring that private data never touches an insecure environment.
Access Flow (Informational Overview)
A general access sequence works like this:
- Connect the hardware wallet to a trusted computer.
- Unlock the device using your personal PIN.
- Open your companion application to view accounts or balances.
- Approve any requested actions directly on the device screen.
- Disconnect the wallet when finished to close access automatically.
This flow defines the secure cycle of local authentication and ensures no remote server ever holds your credentials.
Troubleshooting Login and Access
If your device does not unlock or fails to communicate with the application, begin with the basics: confirm cable integrity, try a different USB port, and ensure firmware and companion software are up to date. If a PIN is forgotten, the device must be reset using the recovery seed. There is no backdoor, vendor override, or remote reset available. This is by design, ensuring that no third party can access user funds.
Security Best Practices
- Keep your recovery seed offline, written on paper or metal, never digitally stored.
- Use a strong, unique PIN and optionally enable a passphrase for advanced privacy.
- Always verify details on the hardware display before confirming a transaction.
- Update firmware only through trusted, official channels.
- Use your device on a clean, malware-free computer whenever possible.
How “Login” Differs from Online Accounts
A key distinction is that Trezor does not operate with usernames or passwords stored on a company server. There is no web-based login or central account recovery option. All authentication happens on the device you hold in your hand. This non-custodial approach means you have full control — and full responsibility — for your security materials.